Zeus virus (Zbot malware): What it is and how to stay protected

The Zeus virus is best known for fueling large-scale financial cybercrime and stealing banking credentials. Although the original Zeus virus is no longer active, it spawned numerous variants that remain a threat today.
This article explains what the Zeus virus does, how it spreads, and ways to tell if your device has been infected. It also examines the virus’s many variants and offers tips on protecting yourself from it.
What is the Zeus virus (Zbot)?
The Zeus virus, also called Zbot, was first detected in 2007. It’s a specific type of malicious software (malware) called a trojan, which disguises itself as a legitimate program to secretly infiltrate a user’s computer. The original Zeus virus affected only Windows computers, but newer variants have been found on Android devices.
Once installed, Zeus does two main things:
- Steals sensitive financial information: Uses form-grabbing and keylogging tactics to record what you type on banking or other financial websites, which it then sends back to a command and control (C2) server controlled by threat actors. This aspect of Zeus is similar to another type of malware called spyware.
- Creates a botnet (robot network): In some cases, Zeus recruits infected machines into a network of compromised devices that can be remotely controlled and used to launch cyberattacks, like distributed denial-of-service (DDoS) attacks, on other targets.
At its peak, Zeus is estimated to have infected 3.6 million machines in the U.S., affecting individuals as well as major financial institutions and government agencies. The widespread impact of Zeus prompted coordinated international law enforcement operations to dismantle its infrastructure, such as Operation Trident Breach in May 2009.
In 2011, it was discovered that the source code for the Zeus virus had been leaked and was being sold on dark web forums. This allowed cybercriminals worldwide to study, modify, and repurpose the malware, leading to the creation of newer and more sophisticated variants. Among the most notorious of these were GameOver Zeus, SpyEye, and Citadel.
These derivatives have ensured that Zeus's legacy persists even into recent years. For example, the Zloader variant was highly active during the COVID-19 epidemic in 2020 when attackers sent emails disguised as government alerts or financial assistance notices to trick users into downloading the malware.
How does the Zeus virus infect computers?
Unlike some types of malware, Zeus can’t self-replicate, meaning it can’t spread on its own. The virus therefore relies entirely on users unknowingly downloading or executing it.
Here are two of the most common tactics used by threat actors to spread Zeus:
- Phishing emails: The threat actor pretends to be a trusted individual or institution to exploit your trust. For example, attackers often trick victims into clicking a link to a malicious website or opening a file infected with Zeus by disguising their emails as financial communications, such as invoices, orders, or receipts. Phishing email attacks are at the root of over 90% of successful cyberattacks.
- Drive-by downloads: The threat actor creates a web page that automatically installs malware onto your device when visited. These attacks often use exploit kits, which are pre-packaged tools designed to take advantage of vulnerabilities in browsers or outdated software. This type of attack is especially dangerous because it doesn't require you to accept a download or open a file; simply clicking on the wrong link is enough.

Once Zeus infects a device, it uses several clever techniques to hide itself and avoid detection. These include:
- Delayed unpacking and anti-analysis tricks: Zeus often keeps parts of its code encrypted and only activates them after a delay. That helps it slip past quick scans and automated “sandbox” tests that only observe a program for a short time.
- Hooking into system processes and browsers: Zeus intercepts normal functions in Windows and web browsers so it can monitor or alter activity in real time. That lets the malware capture or manipulate data inside browser sessions, even those protected by HTTPS.
- Form grabbing: Traditional keyloggers record everything you type, creating large logs that can look suspicious when sent to attackers. Form grabbing captures the exact data entered into a web form right before it’s encrypted and transmitted to the legitimate site. Because that data travels via normal web channels, it’s much harder for security systems to distinguish the theft from regular traffic.
Zeus malware variants
Variants of Zeus often improve upon the original, adding features to help it evade detection and overcome new security measures. Here’s a quick overview of a few of the most notable variants of the Zeus virus.
GameOver Zeus
The GameOver Zeus variant appeared around 2010. It was used for banking credential theft and to distribute the CryptoLocker ransomware, and it resulted in estimated losses of over $100 million.
Unlike its predecessor, which relied on a central server to control infected computers, GameOver Zeus used a peer-to-peer (P2P) network. In this setup, infected computers communicate directly with each other, so there is no single server for authorities to target. This decentralized structure made the botnet much harder to dismantle.
The scale and impact of GameOver Zeus prompted a coordinated international effort to disrupt its operations. In May 2014, Operation Tovar was launched, involving law enforcement agencies and security experts from multiple countries. The operation successfully disrupted the botnet, leading to the seizure of critical infrastructure.
SpyEye and related malware
SpyEye is another notorious Zeus virus variant. Like Zeus, it targeted online banking accounts, but SpyEye added more advanced and customizable tools. These included options to target specific banks, automatically steal funds, manipulate banking websites, and remain hidden from security software.
The malware was widely distributed through spam emails, infecting hundreds of thousands of computers. Operators also used the infected machines to sell stolen credit card information to other cybercriminals, extending the reach and impact of the malware.
Law enforcement eventually shut down the SpyEye network, prosecuting those responsible and seizing the infrastructure used to distribute the malware. These efforts effectively ended the major SpyEye operations.
Citadel
First detected in 2011, Citadel was a sophisticated evolution of the Zeus banking trojan that focused on harvesting credentials, particularly those stored in password managers.
What made Citadel unique was that it was designed to be accessible to a wider range of cybercriminals through a Malware-as-a-Service (MaaS) model. Its developers offered a platform that allowed users to request new features, submit bug reports, and even create their own modules, leading to rapid adoption across multiple botnets.
Its modular design also allowed developers and customers to add capabilities such as improved encryption, screen capture, and anti-detection measures, making the malware both versatile and resilient. At its peak, over 11 million machines were estimated to be infected, causing more than $500 million in losses.
Law enforcement eventually dismantled key parts of the Citadel operation, making key arrests in 2015 and 2017 that led to its decline.
Legacy and influence of Zeus on modern malware
Zeus is one of the most influential banking trojans in history. The leak of its source code in 2011 had far-reaching consequences. Cybercriminals reused and adapted its core features, including credential theft, browser-based web injection, and botnet capabilities, to create numerous variants. These techniques helped define the architecture and operational methods of modern banking trojans, influencing a wide range of successors that targeted both banking and other online services.
The source code release also contributed to the rise of a commercialized malware model. Some derivatives were packaged and sold through underground markets with technical support and updates, making it easier for less technically skilled criminals to deploy sophisticated malware. This approach set a precedent for the professionalized, service-oriented distribution model that continues to shape modern banking trojans.
Symptoms of a Zeus virus infection
While the original Zeus malware is no longer active, its many variants still circulate and can cause similar symptoms. Zeus infections are difficult to spot because the malware is designed to run quietly in the background. Still, there are some warning signs that may point to a compromised system.
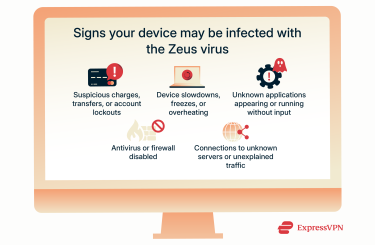
One of the most serious is unexplained financial activity. If you use online banking and notice charges, transfers, or withdrawals that you didn’t authorize, your login details may have been stolen by Zeus. In some cases, attackers can even lock you out of your own account by changing your password once they gain access.
Other symptoms include:
- Performance problems: Zeus consumes system resources in the background, which may cause your device to slow down, freeze, or overheat.
- Strange new files or programs: The malware can install additional malicious software, so you should investigate if you find unfamiliar files or programs running that you don’t remember downloading.
- Disabled security software: Zeus is capable of turning off antivirus and firewall protections, leaving your device more vulnerable.
- Unusual network activity: Infected devices may connect to unfamiliar servers or generate large amounts of traffic you didn’t initiate, either as stolen data is transmitted or as part of botnet operations.
- Sudden changes to system settings: This can include alterations to your desktop background, browser homepage, or search engine.
- Disk issues: You may experience unexplained loss of disk space as Zeus can download additional malware, store stolen data locally, or create temporary files to facilitate its operations.
How to remove the Zeus virus
Here’s a comprehensive guide to removing the Zeus virus (or its subsequent variants) from your device and preventing further damage.
Immediate steps if you suspect infection
If you suspect your device is infected with Zeus, you should act immediately:
- Disconnect from the internet to prevent the malware from communicating with its control servers or sending out sensitive data.
- Change your passwords for any accounts that you believe may have been compromised. Do so on a clean, uninfected device, so your new passwords don’t get intercepted.
- Notify your bank if you notice unexplained financial activity. They can help monitor your account and may even be able to recover lost funds.
- Back up important files to avoid permanent data loss, as some Zeus variants can install ransomware or delete files.
- Seek professional help from a cybersecurity expert if you’re not confident about removing the malware safely or the infection persists despite your efforts.
Using antivirus and anti-malware solutions
The easiest way to remove the Zeus virus is to use an antivirus and malware removal tool. These programs can identify malicious files, quarantine infected programs, and repair changes the malware may have made to your system.
To do so, just follow these 3 simple steps:
- Install a reputable antivirus or anti-malware program.
- Run a full system scan.
- Follow the program’s instructions carefully to remove any malware it finds.

Manual removal methods (advanced users)
Manually removing Zeus is complex and risky and should only be attempted by users with technical expertise. Deleting the wrong system files or making incorrect changes can damage your device, and missing even a single component can allow Zeus to persist or reinstall itself. Additionally, there are many variants of Zeus, which may behave differently.
Here are the general steps involved in manually removing Zeus from an infected device:
- Boot into Safe Mode: Restart the system so that only essential processes are running. This limits the malware’s ability to hide or block removal actions.
- Identify and disable suspicious processes and services: Use advanced process tools, like Process Explorer, to locate unknown or blank-named processes that may be linked to Zeus. This can include hidden threads or dynamic-link libraries associated with the malware. Once suspicious processes are identified, terminate or pause them so the malware is no longer actively running.
- Disable startup entries and autostart components: Use tools like Autoruns to detect and disable any entries in the registry Run keys, scheduled tasks, or the startup folder that reference suspicious files. This prevents Zeus from automatically running after a reboot.
- Delete infected files: Carefully remove executable or library files linked to Zeus from system directories (e.g., %SystemRoot%, %Temp%, AppData).
- Clean registry entries and system changes: Remove any registry keys or configuration changes introduced by the malware to persist, such as modified host files, network settings, or userinit entries.
- Reset browser settings and remove injected scripts: Some variants inject scripts into browsers or alter settings. Restore default browser configurations, remove suspicious extensions, and clear caches to eliminate residual malware activity.
- Restart, monitor, and validate: Reboot the system normally. Monitor network activity or logs to check that no hidden components are reloading.
If you’re unsure about any step or any symptoms of the Zeus virus persist, it’s safest to consult a professional.
How to protect yourself from the Zeus virus
Preventing an infection is preferable to removing malware, and it requires a combination of vigilance, good habits, and reliable security tools. These cybersecurity best practices can significantly reduce your risk of encountering Zeus.
Importance of antivirus and anti-malware tools
Antivirus software can help protect you against malware like the Zeus virus. Those that offer real-time protection continuously monitor your computer's files, processes, and system memory to stop malware before it has a chance to do any damage. If your device is already infected, they can also help you remove the malware.
Securing banking and login credentials
Use strong, unique passwords for each account. A strong password is long and random and includes uppercase and lowercase letters, numbers, and symbols. If you have trouble remembering your passwords, consider using a password manager, like ExpressVPN Keys, which can securely store and autofill login credentials.
Additionally, enable multi-factor authentication (MFA) on your accounts. MFA adds an extra layer of security by requiring a second form of verification to log in, such as a code sent to your phone or generated by an authentication app, in addition to your password.
Keeping software and systems updated
Common tactics used to spread the Zeus virus, like drive-by downloads, exploit outdated programs or security vulnerabilities. Keeping your apps and operating system updated helps close these security gaps.
Awareness of risky links and downloads
Avoid clicking on suspicious links or attachments in emails and messages. Even just visiting a compromised site may be enough to infect your device with Zeus. Be especially wary of messages that are unexpected or attempt to create a sense of urgency.
If you’re ever unsure if a link is safe, you can preview the destination URL by hovering over the link (on desktop) or long-pressing it (on mobile) to preview the URL.
Read more in our guide to preventing phishing attacks.
Use a virtual private network (VPN)
A VPN can complement antivirus software by encrypting your internet traffic and hiding your IP address, making it harder for cybercriminals to perform man-in-the-middle (MITM) attacks that could deliver malware like Zeus. ExpressVPN also provides an extra layer of security via its advanced protection features, which can block malicious ads and websites.
Make regular backups
Some Zeus variants can install ransomware, a type of malware that locks your files and holds them hostage. Back up important data to secure offline drives or cloud storage to ensure that you can recover without losing critical information.
FAQ: Common question about the Zeus virus
Which Zeus malware variants are considered the most dangerous?
GameOver Zeus, SpyEye, and Citadel are some of the most dangerous variants of the Zeus malware. GameOver Zeus used a decentralized peer-to-peer (P2P) network, making it harder to take down. SpyEye added customizable tools to target specific banks and automate financial theft. Citadel combined modular architecture with a service-oriented distribution model, which enabled widespread deployment. Together, these variants caused substantial financial losses worldwide.
Can Zeus malware also infect mobile devices?
The original Zeus malware targeted Windows PCs. But newer malware inspired by Zeus after its source code was made public in 2011 has been found on Android devices.
Which antivirus and security tools work best against Zeus?
You don’t need a specific antivirus or security tool to detect and remove Zeus from your device. Any reputable antivirus and anti-malware tool with real-time protection, up-to-date virus definitions, and full system scanning capabilities can help.
Is the Zeus virus still an active threat today?
The original Zeus virus is no longer an active threat. However, when its source code was made public in 2011, it inspired a host of new malware based on Zeus, and some of these threats are still active today.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN