Shellshock: What you need to know and how to protect yourself from the bash bug

A deadly bug with the ability to affect hundreds of millions of computers, servers and other devices has been discovered in the wild.
What do you need to know about Shellshock?
Dubbed ‘Shellshock’ by the media, the bug was discovered in Bash, a command shell program found in UNIX-based systems. In this article, we show you what you need to know; as well as how to protect your machine from this bug.
Those of you who are not familiar with Bash, or think you don’t use it, should consider for a moment that a vast array of devices are vulnerable including routers, internet of things devices, Apple Macs, Linux-based systems and web servers.
The flaw, known as a Remote Code Execution (RCE) vulnerability, can be used to take control of almost any system using Bash up to and including version 4.3.
Due to the widespread use of Bash, the real concern is that malware authors could exploit the vulnerability by creating a fast-spreading worm, though the attacks we’ve seen so far have tended to centre around botnet creation and DDoS attacks, password extraction tools and data exfiltration.
The bug (known as CVE-2014-6271) was first discovered on September 12 by Stephane Chazelas but was not disclosed until September 24 to allow time for security updates to be prepared before publication.
Subsequent analysis of the bug shows that it has been in existence since around version 1.13 to version 1.14 which were released between 1992 and 1994. While there have been no reported instances of the bug being exploited over the previous 22 years, the irony of disclosure is that attacks are very much prevalent now with AlienVault reporting that attacks which attempted to install malware onto target systems, as well as vulnerability detection attempts against honeypots it specifically set up, started almost as soon as the Bash vulnerability was publicised.
Just like Heartbleed back in April, Shellshock has the potential to affect large number of systems, though the latter is anticipated to pose a threat to half a billion machines around the world in comparison to the 500,000 thought to have been susceptible to Heartbleed.
Besides potentially affecting far more machines than Heartbleed, Shellshock also poses a bigger danger too in that it allows an attacker to have direct access to a system instead of merely pulling information from it.
What do you need to do to protect yourself from Shellshock?
Systems that haven’t updated Bash since September 28 2014 are likely to be vulnerable and this can be confirmed by running your own self-test.
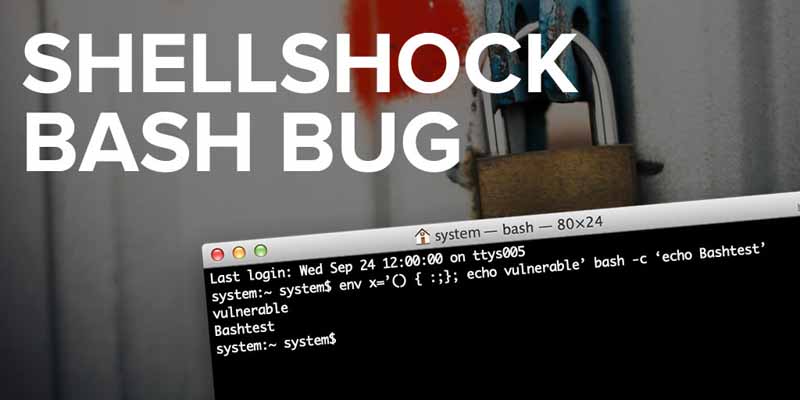
To do this, open a terminal window and type the following command at the $ prompt:
env x='() { :;}; echo vulnerable' bash -c 'echo Bashtest'
If your system is safe from the vulnerability then you’ll see this:
bash: warning: x: ignoring function definition attempt bash: error importing function definition for `x’ bashtest
If you are not so fortunate, and have a vulnerable system, you will see the following instead:
vulnerable Bashtest
To further check if your system is vulnerable, we have found a useful tool at Shellshocker.net that allows you to test specific http or https URLs, along with a list of commands that can be used to test for specific Bash-based exploits.
If your system is found to be vulnerable, you should update immediately, despite the fact that patches are not running 100% flawlessly yet, as that will afford you at least some extra protection.
If you require the latest patches then the US CERT alert page contains several handy links at https://www.us-cert.gov/ncas/current-activity/2014/09/24/Bourne-Again-Shell-Bash-Remote-Code-Execution-Vulnerability.
And if you are under any illusions as to the severity of the bug, I’ll leave the last words to CloudFlare CEO Matthew Prince who recently highlighted in a Tweet what happened straight after the Shellshock bug was disclosed:
“In case anyone is curious, we're seeing north of 1.5 million #shellshock attacks across the @CloudFlare network daily.” If you would like to learn more about Shellshock we highly recommend Troy Hunt’s comprehensive analysis.
Here at ExpressVPN we started investigating all possible fixes to the Shellshock Bash Bug as soon as the bug was first disclosed on September 24, and have been patching our systems as soon as updates are released. Click here to read our announcement for more. Stay safe everybody!
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN