How to recover a hacked Google account

If someone has taken over your Google account, you're not alone. And while it’s a worrying situation, you’re not powerless. There are steps you can take to recover your account, even if the password has been changed.
In this guide, we’ll help you spot the signs of a hack, explain why these breaches happen, and describe what you can do to secure your data moving forward. Whether you're locked out of Gmail or see suspicious logins, you'll find practical, Google-aligned advice to get back in and protect your account from future attacks.
Signs your Google account might be hacked
If your Google account has been compromised, there are usually warning signs. Pay attention to the red flags below.
You receive unfamiliar security alerts
A common sign that your Google account might be at risk is receiving a security alert about unfamiliar activity. Google sends notifications to your email or phone if there’s an attempt to log in from a new device, a password change, or if an unusual number of emails are sent from your account, for example.
If you receive a notice you didn’t trigger, it may indicate unauthorized access. These alerts are meant to prompt quick action to prevent potential harm.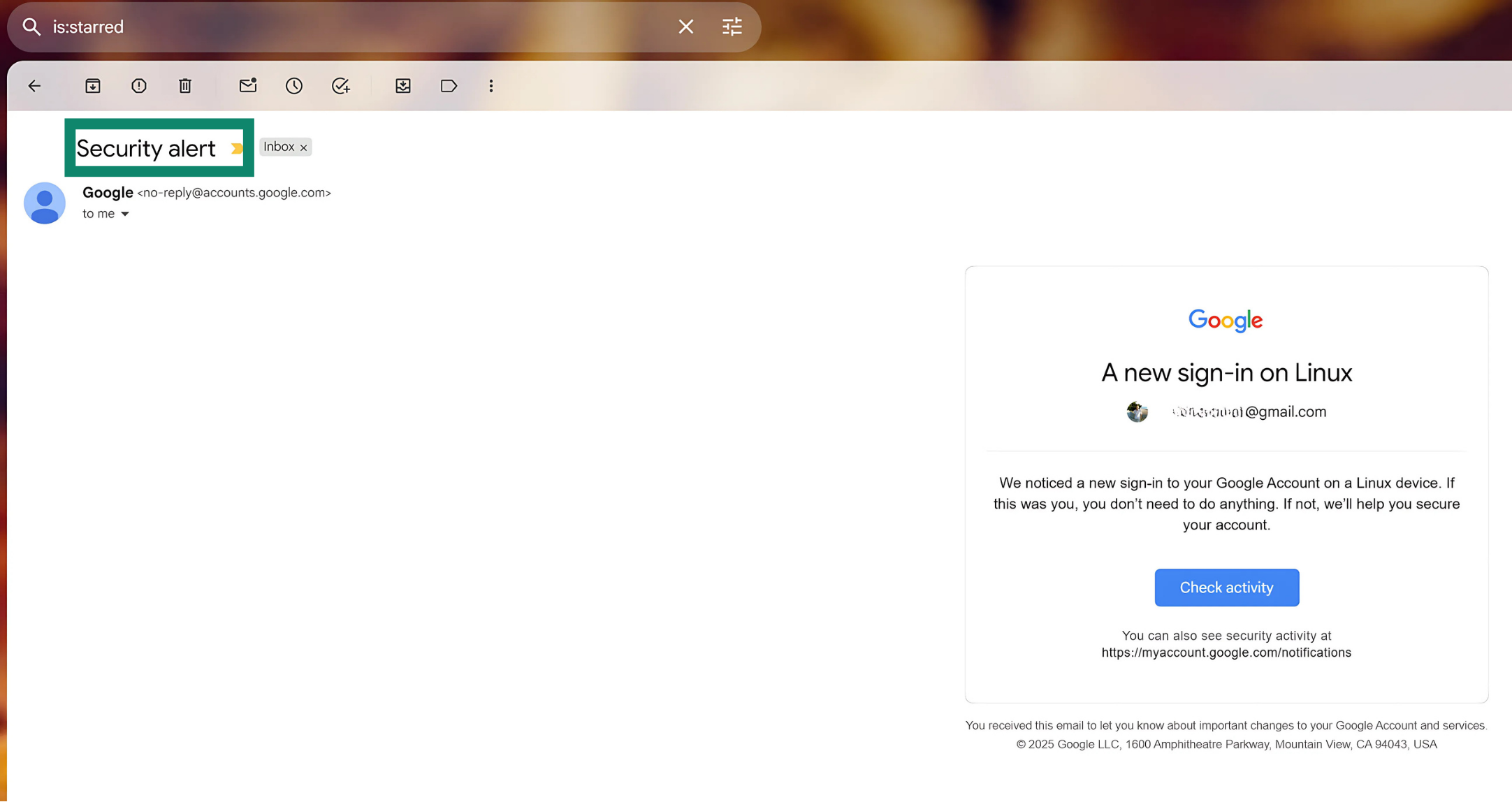 You’ll also get an alert if Google blocks a sensitive action, like someone trying to view your saved passwords. Just be cautious: scammers sometimes send fake alerts, so it's important to verify the legitimacy of any message by checking your Google account settings for a matching alert.
You’ll also get an alert if Google blocks a sensitive action, like someone trying to view your saved passwords. Just be cautious: scammers sometimes send fake alerts, so it's important to verify the legitimacy of any message by checking your Google account settings for a matching alert.
Suspicious logins from unknown locations or devices
Google keeps a record of the devices and locations that have recently accessed your account. If you notice unfamiliar locations (for instance, countries you’ve never been to) or strange devices logged in, that’s a major red flag.
This kind of device activity often signals that someone has guessed or stolen your password and is accessing your account without your knowledge. You can check this through Google’s Security Checkup tool, which provides a clear list of all recent account activity.
Password changed without your knowledge
If your regular password suddenly stops working, and you didn’t request a Google password reset, it could mean that someone else has changed it. A cybercriminal who gains access to your account will often change the password right away to lock you out and gain control.
As such, it’s important not to lose access to the backup email or phone number used for recovery. Also, if you reused an old or previously exposed password for your Google account, that might be how the cybercriminal got in; this is a good reason to use a strong, unique password for every account.
Emails sent from your account without your action
If people you know are receiving strange emails from your Gmail address, especially messages with suspicious links or attachments, that’s a strong sign your account has been hijacked.
Cybercriminals often use compromised email accounts to spread phishing scams or malware, relying on the trust of your contacts to get them to click. You may also find unfamiliar messages in your Sent folder or spam complaints you didn’t expect.
Linked apps or services you don’t recognize
Sometimes, unauthorized access doesn’t come from a person but from third-party apps or browser extensions that have been granted permission to use your Google account. These apps can view your emails, contacts, calendar, and more.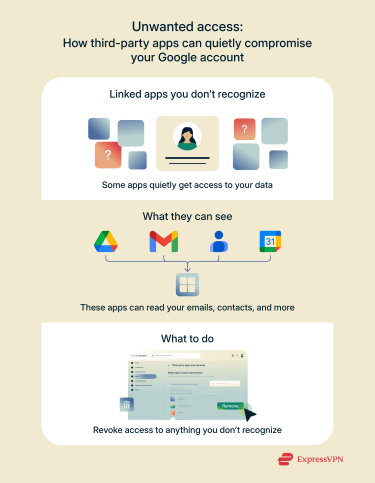 If you notice services linked to your account that you don’t recognize, it's worth revoking their access. This kind of access can be subtle and easily overlooked, but it’s often used to gather personal data quietly over time.
If you notice services linked to your account that you don’t recognize, it's worth revoking their access. This kind of access can be subtle and easily overlooked, but it’s often used to gather personal data quietly over time.
Unauthorized financial activity
A more serious consequence of a hacked account is fraudulent charges on services linked to your Google account, like Google Pay, Google Play, YouTube Premium, or Google Ads. If your saved payment methods have been misused, you may see unfamiliar subscriptions, purchases, or ad spending.
These financial red flags point to a cybercriminal exploiting your account not just for data, but for monetary gain.
Step-by-step: How to recover a hacked Google account
1. See if you can sign in to your account
Go to Google sign-in and see if you can still access your account. If you're blocked, you'll be prompted to recover it. If you can access your account, immediately change your password and recovery email, phone number, and two-factor authentication (2FA) settings to minimize damage.
2. Go to Google Account Recovery
Go to Google Account Recovery and follow the prompts. If a cybercriminal has changed your login details, this tool is the best way to reclaim your Gmail and remove unauthorized access. To improve your chances, use a device, browser, and location you’ve signed in from before (Google recognizes familiar patterns).
3. Verify your identity with available recovery methods
To confirm that you're the rightful account owner, Google will ask you to verify your identity using the recovery options you've set up. This may include entering a verification code sent to your recovery email or phone number.
You’ll also be asked questions about old passwords, answers to security questions, or details such as when you created the account. If prompted, enter your recovery phone number or email so Google can send a code to verify your identity. The more accurate your responses, the more likely you’ll regain access.
4. Change your password immediately
If you managed to recover access to your account, you should start by changing your password. When creating a new password, make sure that it’s strong and unique. Reusing old passwords increases the risk of further compromise. With that said, here’s how to do it:
- Open your Google account.

- On the side panel, select the Security tab.
- Select the Password option.
- Create a new password and click on the Change Password button.
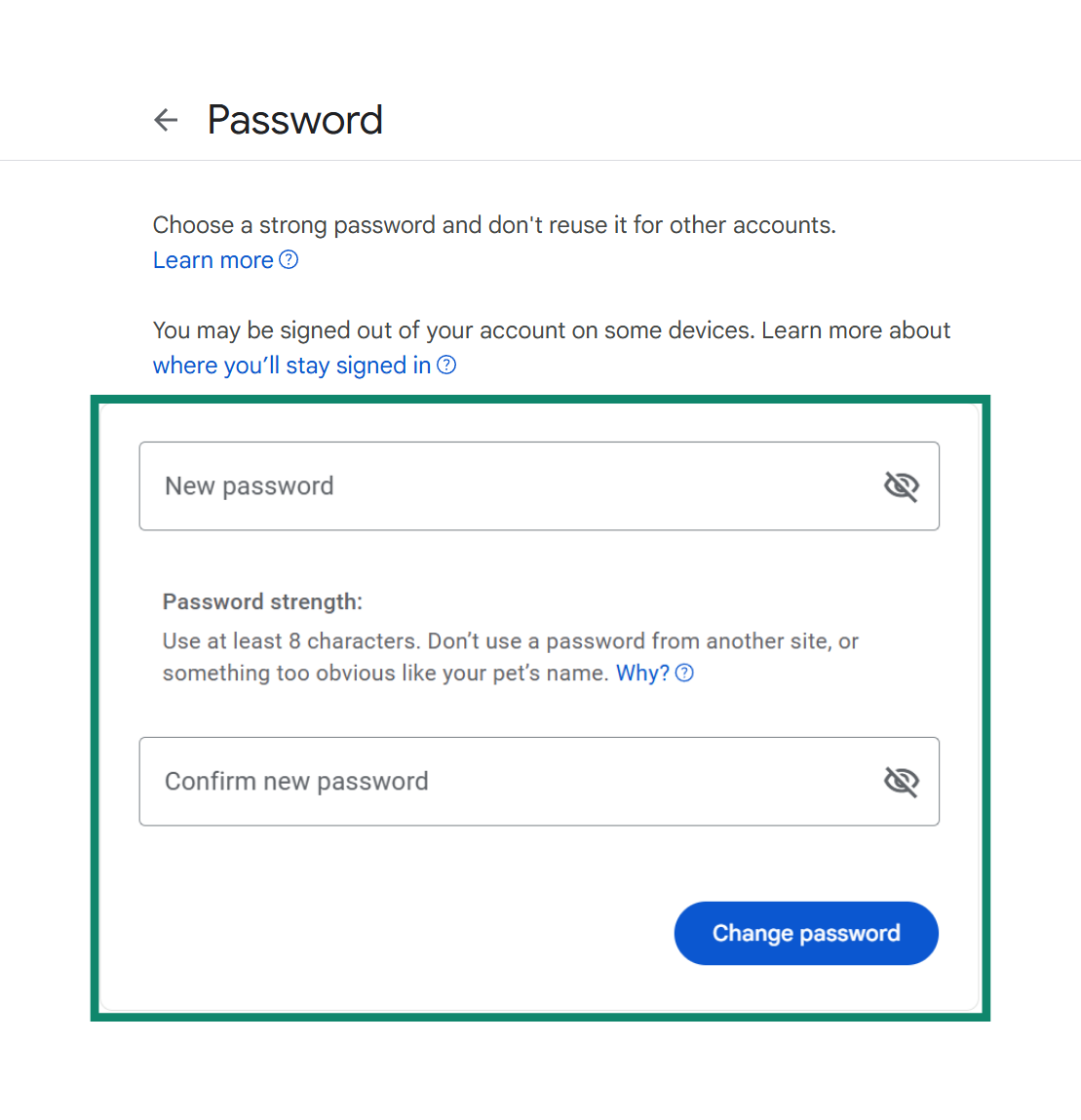
If you need help creating a secure password, this guide to changing your Google password walks you through the steps and best practices.
5. Remove unauthorized devices and apps
If someone has gained unauthorized access to your Google account, they may have connected a device to monitor your activity or change your settings without your knowledge. Reviewing and removing unfamiliar devices is one of the fastest ways to secure your account and stop ongoing access. Here’s how to do it:
- Go to your Google account.

- Select the Security tab from the left-hand menu.

- Scroll down to the Your Devices section and click on Manage all devices.
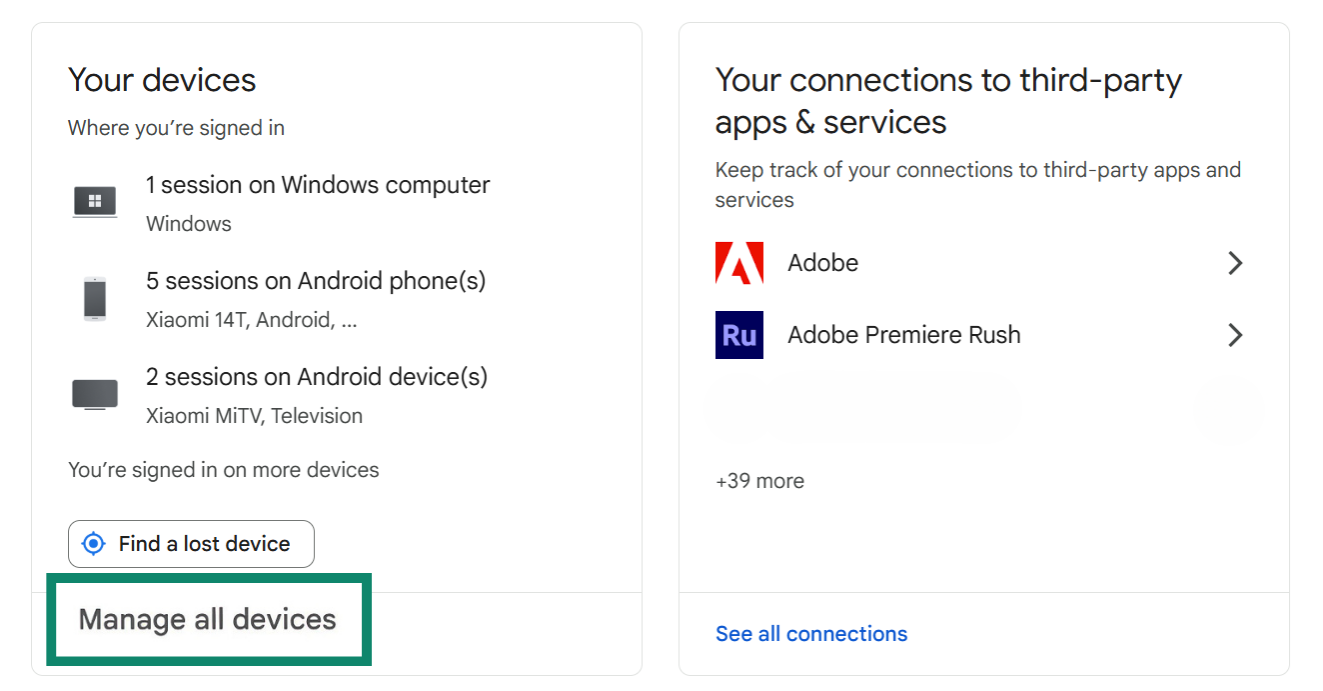
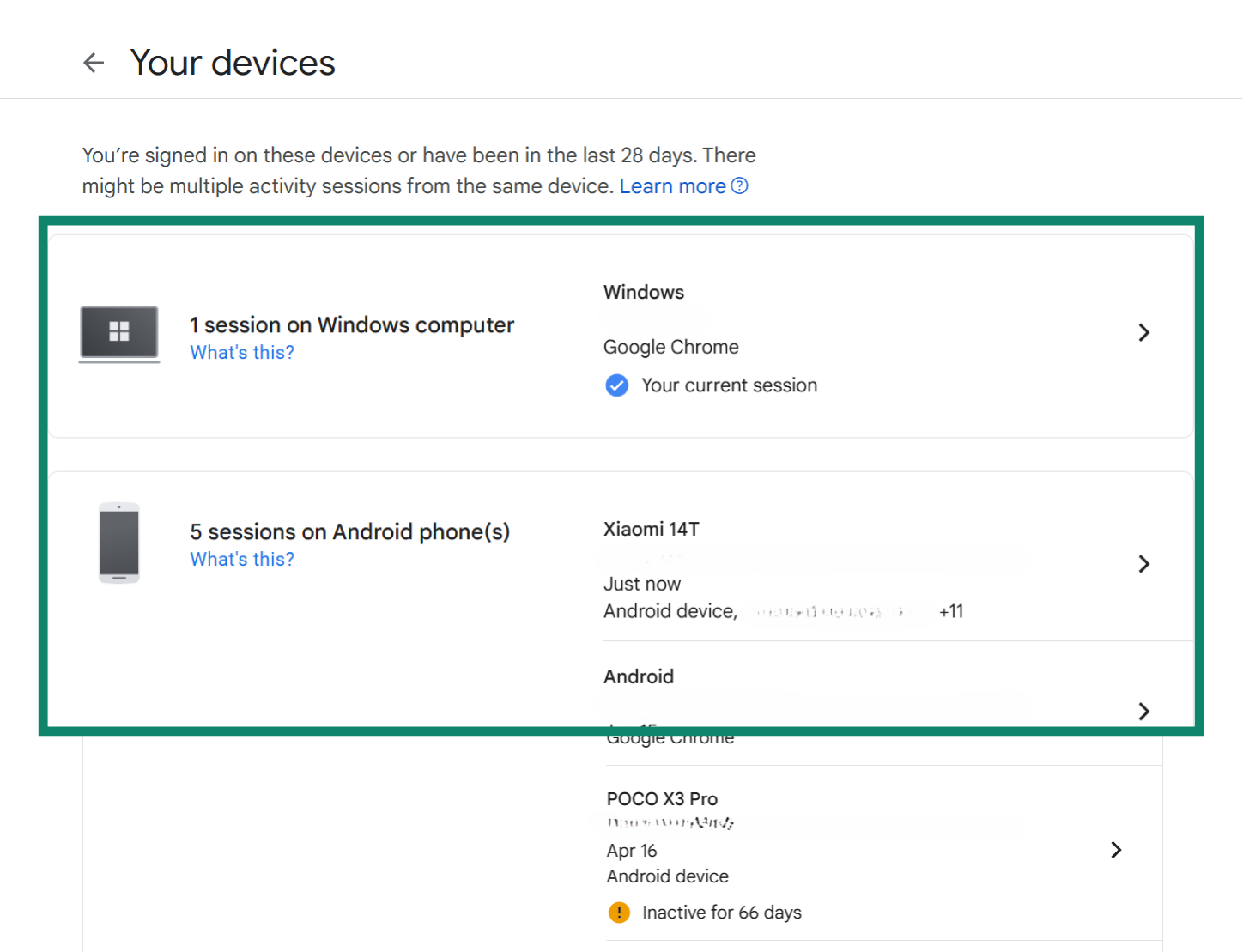
- Select any device from the list that you don’t recognize.
- Click the Sign out button to remove the device from your Google Account.
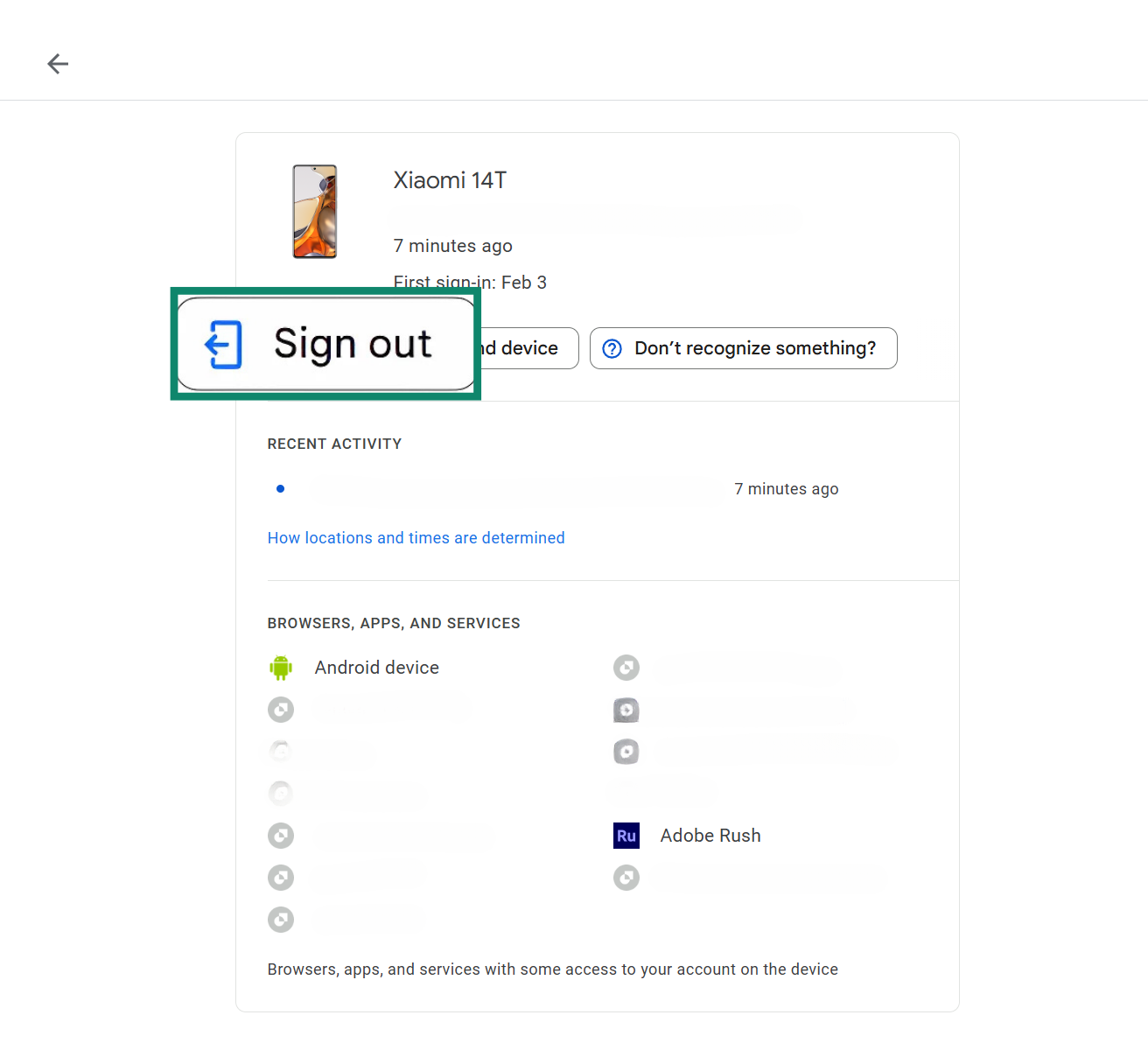
- To remove unwanted access from third-party apps, visit Security and go to Your connections to third-party apps & services.
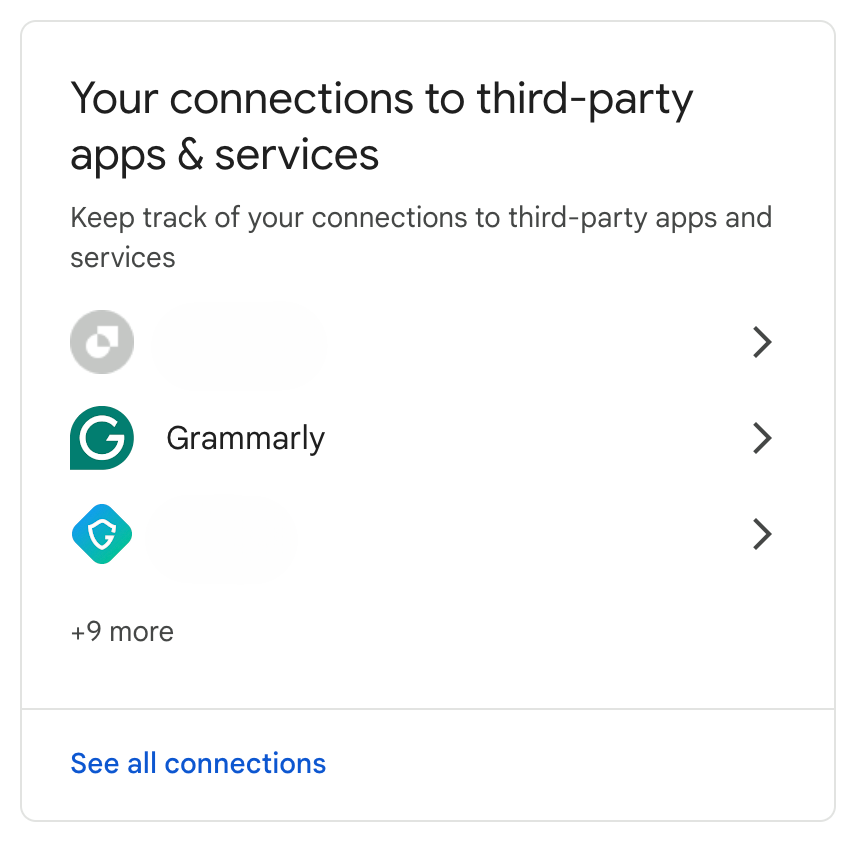
- If you see an unfamiliar app, click on it. This will take you to details of the account access it has. To remove this access, select Delete all connections you have with [the app].
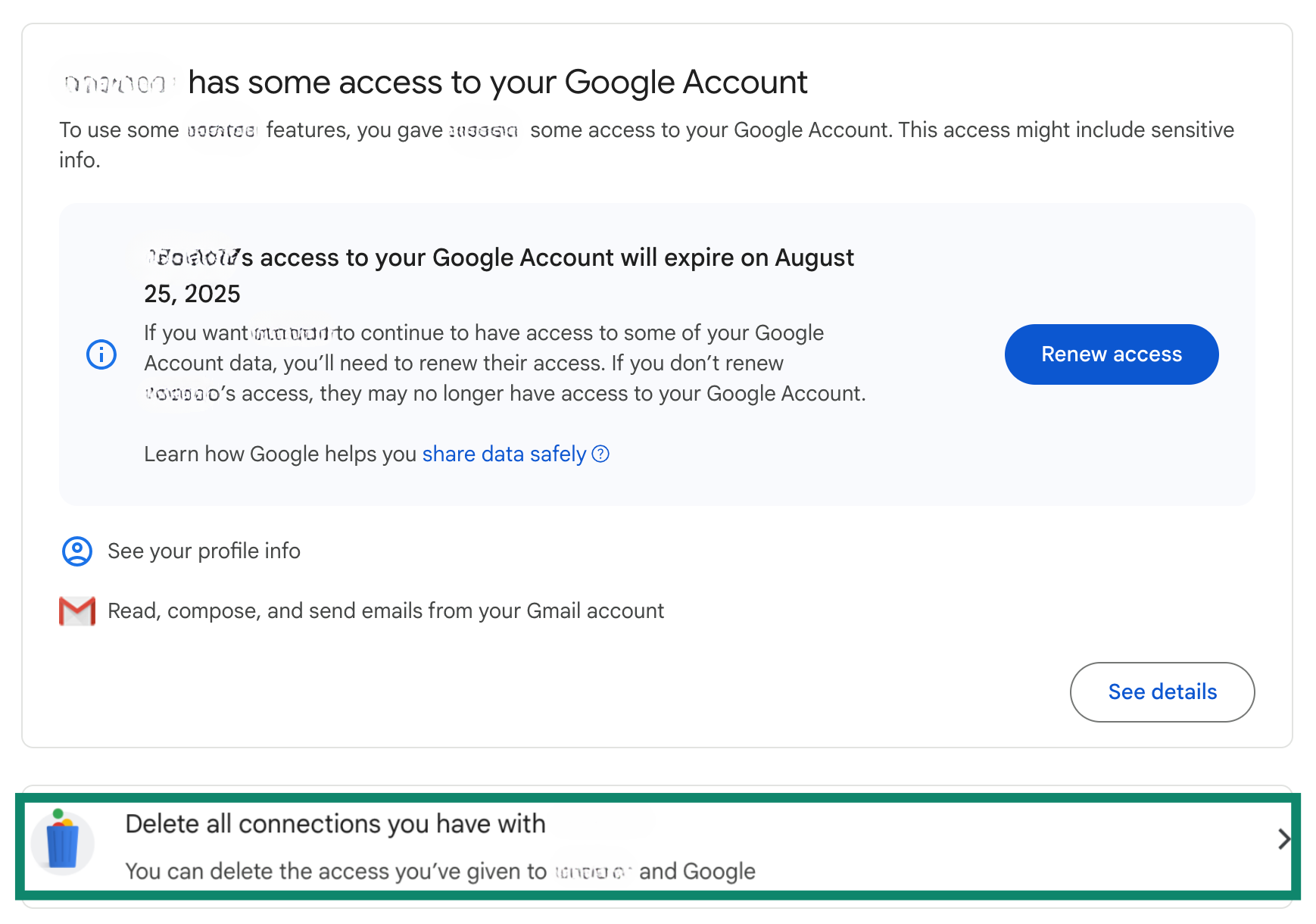
- Choose Confirm to complete the process.
6. Secure your recovery phone and email
Changing your password locks out unauthorized users, but it’s just as important to verify your recovery details. Here’s how to add new recovery methods:
- Go to your Google account.

- Select the Security tab from the left-hand menu.

- Scroll down to the How you sign in to Google section and click on either Recovery phone or Recovery email.
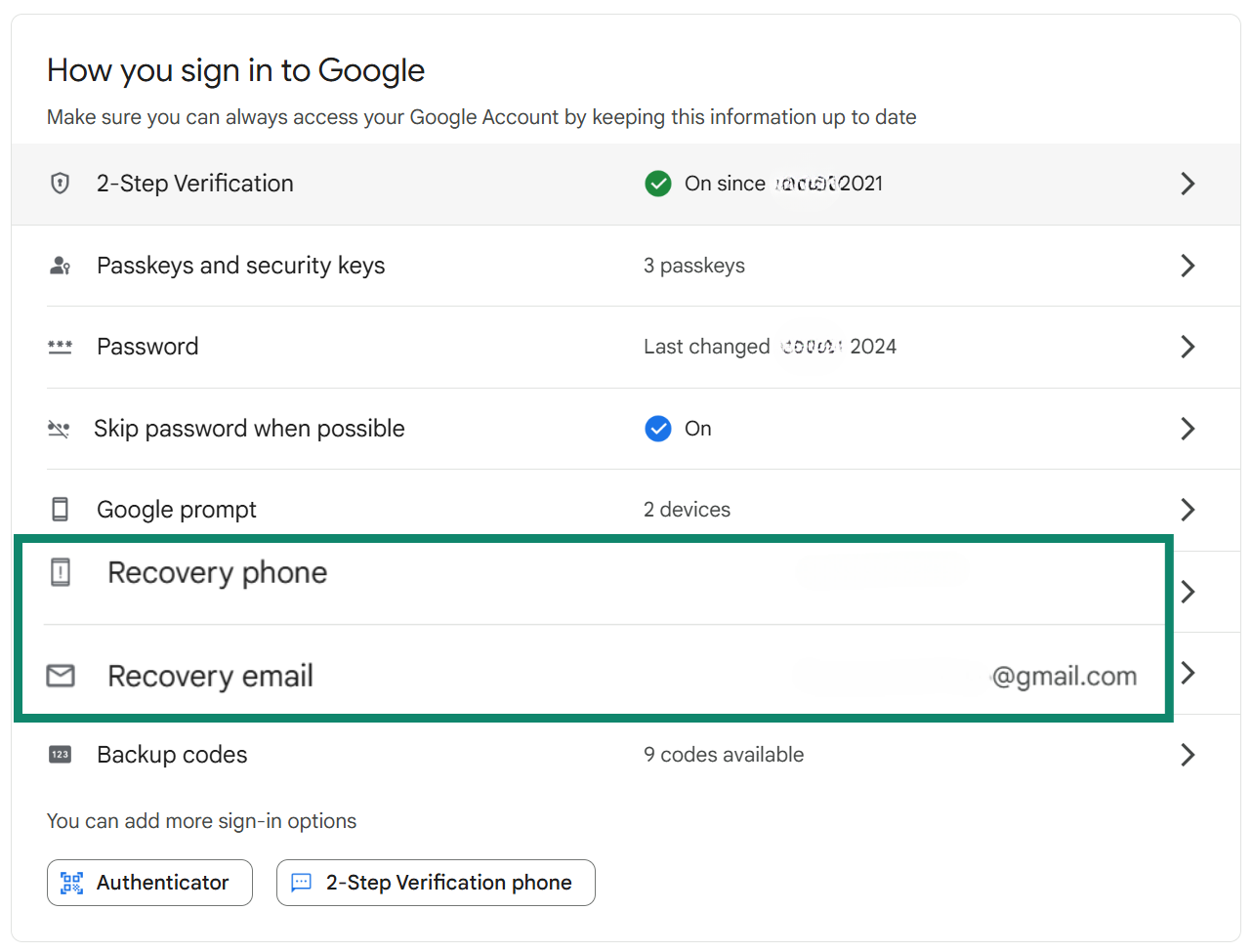
- If either one is outdated or unfamiliar, click Edit and enter the correct recovery information.
7. Enable 2-step verification (2FA)
Even strong passwords can be compromised, which is why 2FA is so important. It adds an extra layer of protection by requiring a second form of verification, like a code sent to your phone, before anyone can access your account. This makes it much harder for hackers to break in, even if they know your password.
- Go to your Google account.

- Select the Security tab from the left-hand menu.
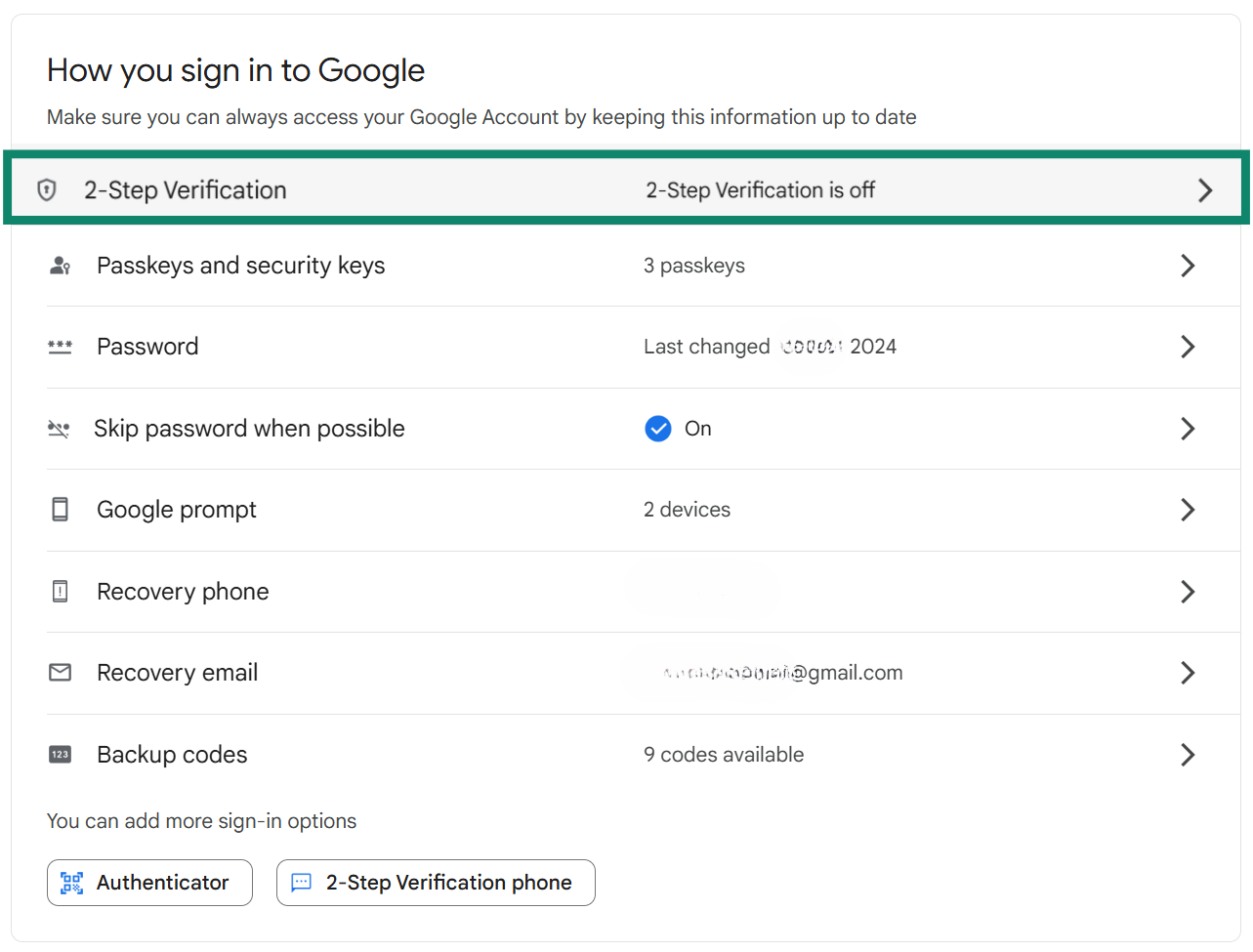
- Scroll down to How you sign in to Google and click on the 2-Step Verification option.
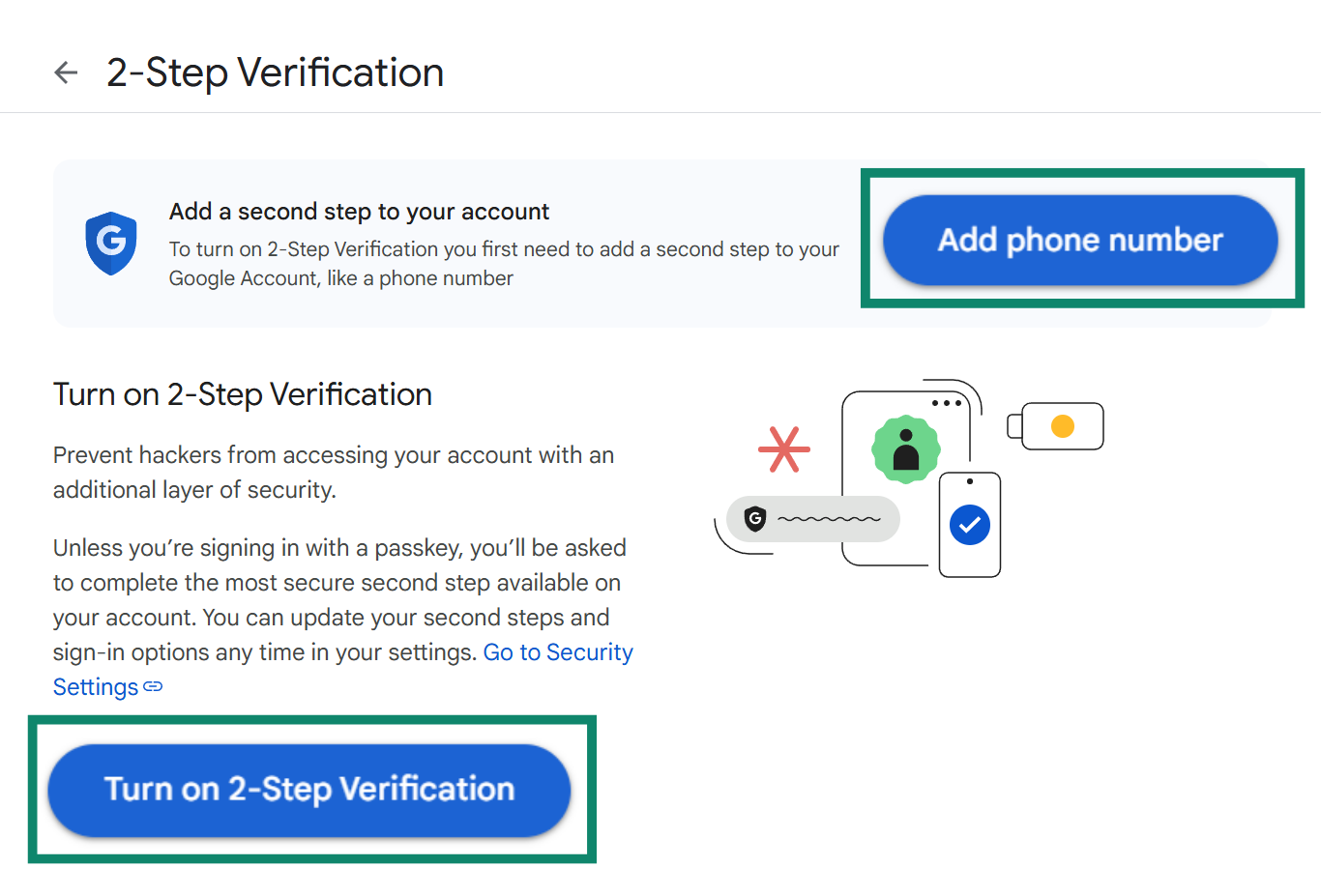
- Select the Add phone number option, and once finished, click on Turn on 2-Step Verification.
Another reliable method is to use Google’s authenticator app, which generates time-based codes on your phone. It doesn’t need a network connection and is harder for attackers to intercept than SMS codes, making it a safe choice for protecting your account.
8. Run an antivirus scan
If your device was compromised, malware could be the culprit, and it might be giving cybercriminals access to far more than just your Gmail. One of the tools cybercriminals may use is keyloggers that record everything you type, including new passwords.
To remove anything suspicious and stay safe, install a trusted antivirus or anti-malware tool and run a full scan on every device linked to your account. If anything suspicious is found, remove it immediately to stop further data theft.
9. Alert authorities if required
If your compromised Google account led to serious consequences, like financial fraud, identity theft, or online impersonation, it’s important to report the incident to your local authorities. Filing a police report creates an official record, which may be needed to dispute unauthorized charges or restore stolen identities. Also, if the hack happened due to a fake Google page, be sure to report the site.
In some countries, you can also report cybercrimes to a national fraud agency or cybersecurity center, like the Internet Crime Complaint Center (IC3) in the U.S.. While not every case requires legal action, involving the proper channels helps protect you and may assist in tracking down the perpetrator.
10. Tell your contacts about the hack
Notify your contacts that your account was compromised, especially if the cybercriminal may have sent spam or phishing messages from the account. A quick message, via text, social media, or a different email account, can help prevent them from clicking on harmful links or sharing sensitive information. It’s a simple step that protects others and helps limit the damage caused by the security breach.
Can't access recovery email or phone number?
If you’ve lost access to your recovery email or phone number, recovering your Google account can feel frustrating, but you're not out of options. These recovery methods are just the first steps Google tries when you say you can’t sign in.
If you no longer use the phone number or email linked to your account, don’t panic. You can still move forward with other verification methods. The key here is to be patient and answer everything as accurately as possible.
Use “Try another way” during account recovery
When you attempt to reset your Google password, you’ll usually be asked to confirm a recovery email or phone number. If these aren’t available to you, Google offers a lifeline: “Try another way.” This option appears after you skip or can’t use the first recovery suggestion. 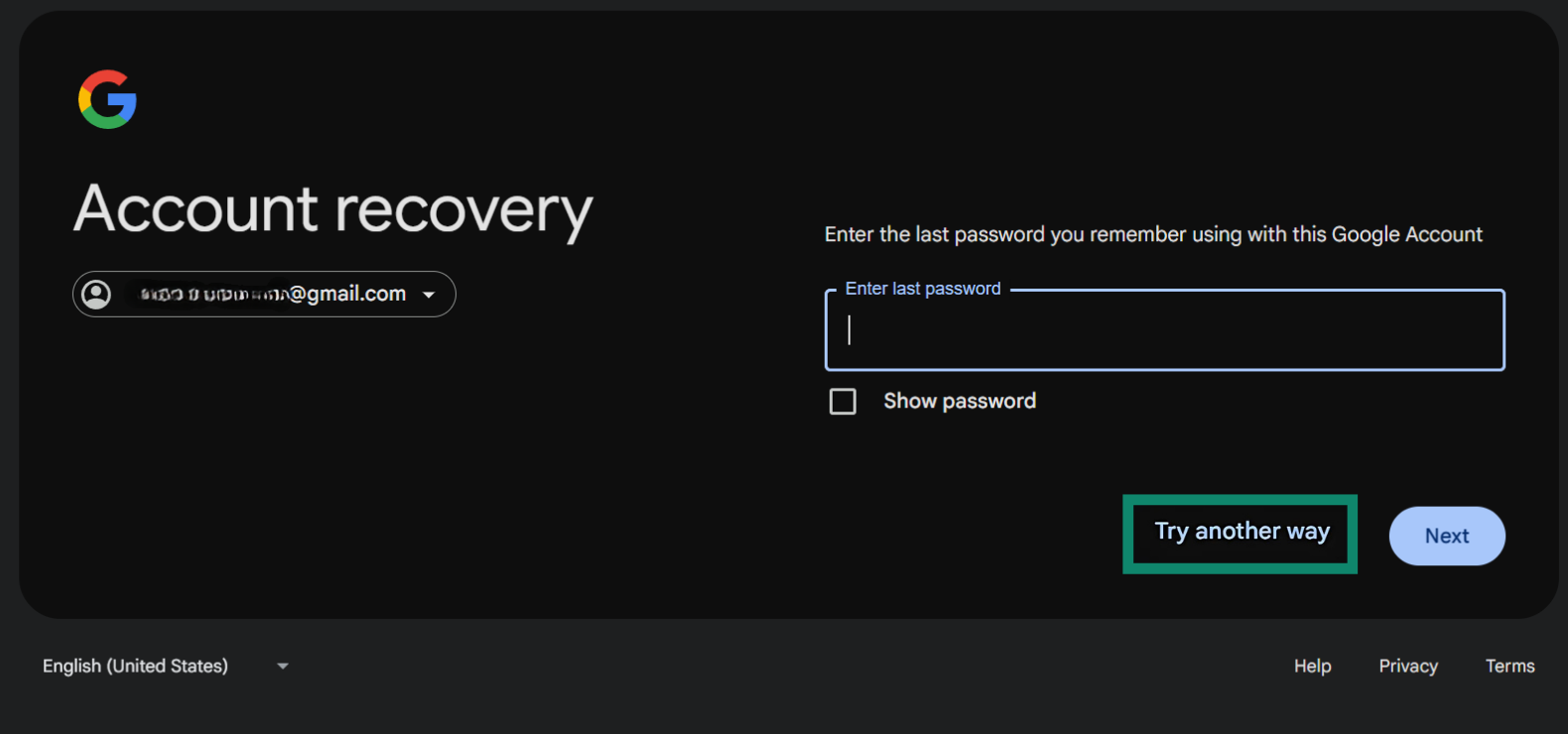 You might be offered options like receiving a code on another device where you're logged in, answering security questions, or confirming when you created the account, but these aren't guaranteed and depend on what you've set up in advance.
You might be offered options like receiving a code on another device where you're logged in, answering security questions, or confirming when you created the account, but these aren't guaranteed and depend on what you've set up in advance.
Depending on your answers, you might have to wait a few hours or a number of days for access. Still, choosing “Try another way” gives you a better shot at recovery, especially if you’ve updated your security settings in the past.
Answer your security questions
Google has largely phased out security questions in favor of more secure methods (like your phone number), so this option is unlikely to appear. If it does, answer exactly as you did when setting up the questions.
Provide last known password and account creation details
Google sometimes asks for your last password. If you can remember any password you used with the account, even if it wasn’t the most recent one, enter it. It helps Google confirm your identity.
You might also be asked when you created the account. Try to recall the month and year. If you can’t remember the exact date, take your best guess, especially if you still have access to old emails or receipts tied to that account. These details build your case that you’re the rightful owner, so the more accurate you are, the better your chances of regaining access.
How did your Google account get hacked?
Getting locked out of your Google account is scary, and the first question most people ask is, how did this happen? In most cases, accounts get compromised due to a security vulnerability, whether that’s clicking a bad link, reusing a password, or getting tricked by someone pretending to be Google.
Understanding how cybercriminals get in can help you avoid future attacks. Most breaches happen silently in the background; you might not notice until it’s too late, which is why staying alert and using strong, unique passwords is so important. Below are the most common ways cybercriminals gain access to Google accounts.
Phishing attacks
Phishing is one of the most common ways cybercriminals steal login information. It happens when someone tricks you into clicking a fake link, usually in an email or text message, that looks like it’s from Google or another trusted company. The page might ask you to log in, but it’s actually capturing your username and password.
Phishing attempts can look almost identical to real Google messages, and it’s getting easier to create convincing ones with the increasing sophistication of AI tools.
The message may warn you about “suspicious activity” or claim your account will be disabled unless you act quickly. That urgency is the trap. If you ever get a message asking you to log in, don’t click the link: go directly to the official site instead. And always check the web address (URL) before entering your login info.
Data breaches and password reuse
If you reuse the same password across multiple websites, a security breach on one site can compromise your Google account, even if Google itself wasn’t hacked. Cybercriminals often get huge lists of usernames and passwords from other companies, then try them on major services like Gmail. For example, if you used the same password on a shopping site years ago and that site was hacked, a cybercriminal could use that password to access your Google account.
To protect yourself, always use a unique password for each account.
Malicious extensions or apps
Some browser extensions and third-party apps can do more than they claim, especially if they ask for access to your Google account. Once installed, a malicious extension can act as a keylogger, which can read your online activity or even steal your login details.
This often happens when people install apps or tools that promise free features or enhancements for Gmail, Docs, or Chrome. If they weren’t made by a trusted developer, they could be a security risk.
If your account was hacked, check your Google Account permissions and remove any apps or extensions you don’t recognize. Going forward, only install apps from developers you trust, and review permissions carefully before granting access.
SIM swapping or number theft
SIM swapping is when a cybercriminal tricks your carrier into giving them control of your phone number. Once they have it, they can intercept your text messages, including verification codes used to access your Google account.
This kind of attack is especially dangerous if you rely on text messages for two-step verification. A cybercriminal can receive the code meant for you and use it to reset your password.
To reduce the risk, switch to using Google Authenticator. It’s a more secure option than using SMS for 2FA. You can also ask your phone provider to add extra security to your mobile number, such as a PIN or account lock.
Using public or unsecured Wi-Fi
Logging into your Google account over public Wi-Fi, like in a café, airport, or hotel, can put your data at risk. If the network is unsecured or set up by someone with bad intentions, your information could be intercepted as you type it. 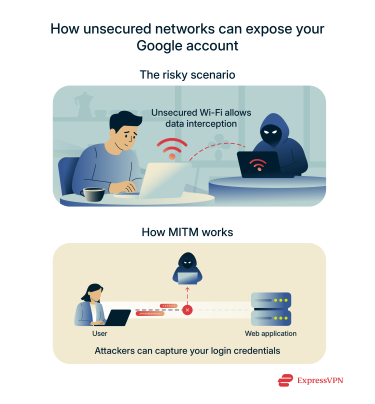 This type of attack is called a man-in-the-middle attack (MITM), where someone on the same network quietly captures what you send and receive. Even though most websites (including Google) use encryption, a poorly secured network still increases the risk of some information slipping through.
This type of attack is called a man-in-the-middle attack (MITM), where someone on the same network quietly captures what you send and receive. Even though most websites (including Google) use encryption, a poorly secured network still increases the risk of some information slipping through.
If you need to use public Wi-Fi, always connect using a VPN, which will encrypt all your data and mask your IP address. This adds an important layer of protection between you and the Wi-Fi network and increases your overall privacy.
What can a cybercriminal do with my Google account?
A compromised Google account is more than just a lost inbox; it’s a doorway into your digital life. Once a cybercriminal gets in, they can access your emails, documents, photos, and even your location history. That means they can learn where you live, who you talk to, and what services you use.
If your account is linked to banking apps, online shopping, or saved passwords, the damage can quickly escalate. A cybercriminal might try to reset passwords on other sites using your email, send phishing messages to your contacts, or even impersonate you for fraud.
They could also download your Google Drive files, wipe your calendar, or lock you out by changing your recovery methods. In short, once someone has access to your Google account, they can do serious harm, both personally and financially.
When to consider deleting your Google account
If you no longer trust that your account is secure, deleting it might be the safest option. This is especially true if sensitive data like ID scans, financial info, or legal documents were stored in your Gmail or Google Drive.
That said, before you delete it, it’s worth using Google’s Security Checkup tool first. This can reveal what parts of your account were accessed, helping you take further protective steps. For example, you’ll see if there are new saved passwords or if there are new apps and services linked to your account. This insight can help you pinpoint the weak point in your digital security.
Finally, download any data you still have access to before deletion. Begin with Google Takeout, a free tool that lets you export a copy of your data from services like Gmail, Google Drive, Chrome, and Calendar.
How to prevent future hacks
Once you've recovered or replaced a compromised Google account, the next step is making sure it doesn't happen again. Most account hacks come down to weak passwords, reused logins, or falling for phishing scams.
In past breaches, Gmail credentials were exposed not because Google was hacked, but because people reused the same password across multiple sites. When one of those sites was compromised, attackers could use the stolen passwords to break into Google accounts. Below, you can find a few simple habits that you can use to dramatically lower the risk of your Google account being compromised.
Use Google’s Security Checkup regularly
Google offers a built-in tool called Security Checkup that walks you through your account’s current safety settings. It shows you if your recovery options are up to date, whether you’re using 2FA, and which devices and apps have access.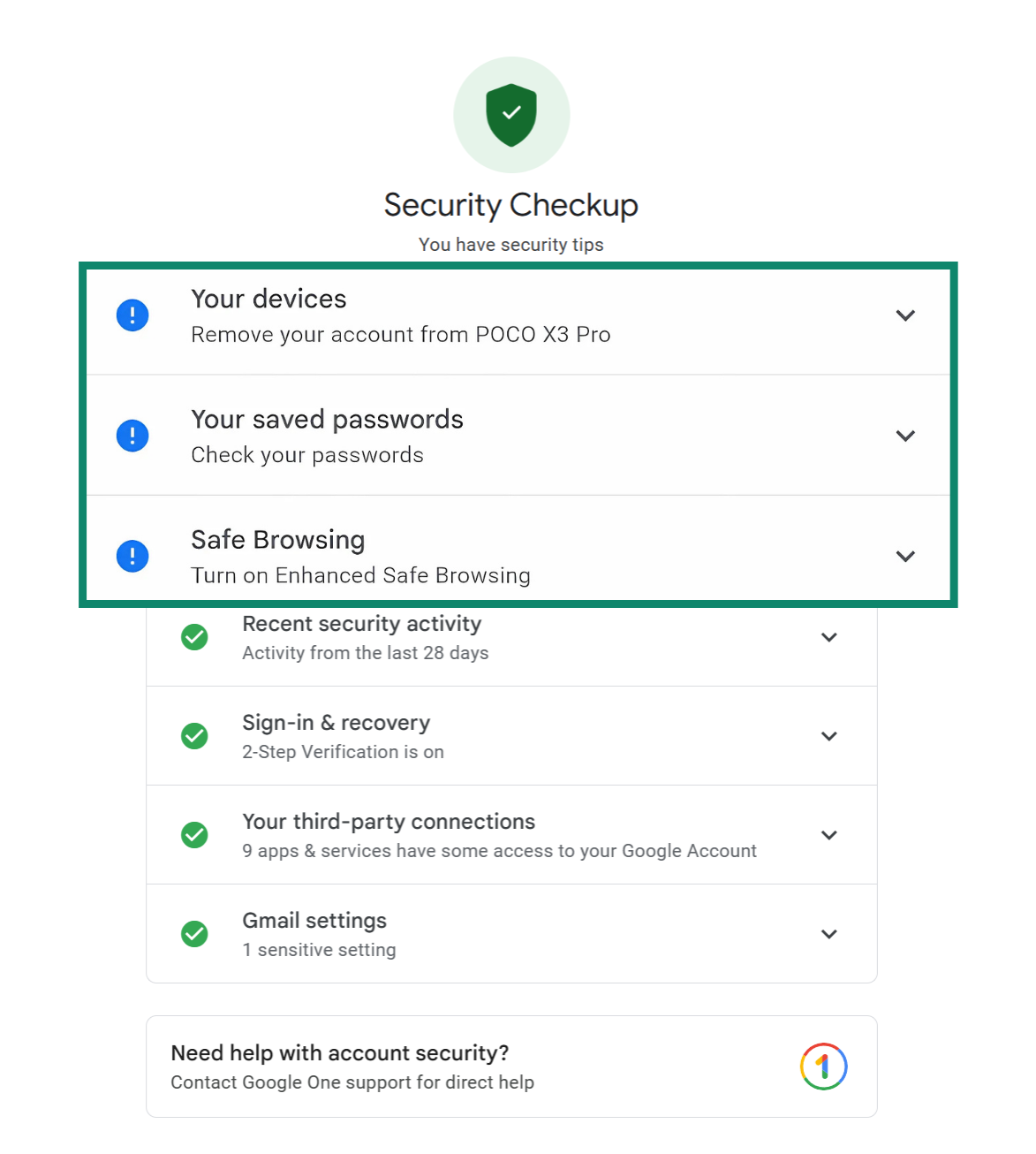 You can run it at any time; it only takes a few minutes, and it gives you personalized tips to improve your account’s security. Doing this check every few months (or anytime something feels off) is an easy way to stay one step ahead of cybercriminals.
You can run it at any time; it only takes a few minutes, and it gives you personalized tips to improve your account’s security. Doing this check every few months (or anytime something feels off) is an easy way to stay one step ahead of cybercriminals.
Use a strong, unique password
Your password is your first line of defense. A strong password should be long (at least 12 characters), hard to guess, and completely unique to your Google account. Avoid anything that includes your name, birthdate, or common word and number sequences like “password123.”
Never reuse passwords across different sites. If one gets leaked, cybercriminals will try it everywhere, including your Google account. To make things easier, consider using a password manager like ExpressVPN Keys. It can create and store strong passwords for every account, so you don’t have to remember them.
Avoid clicking suspicious links or attachments
Most phishing attacks start with a convincing-looking message, often pretending to be from Google, a friend, or a familiar service. These emails or texts often include urgent language and ask you to click a link, download a file, or enter your password. Be especially cautious with unexpected messages that ask you to “verify your account” or “reset your password.”
When in doubt, visit the official site directly instead of clicking the link. To add a layer of protection, tools like ExpressVPN’s Threat Manager can help block access to known phishing or malware-hosting pages before they ever load.
Finally, avoid downloading attachments from unfamiliar senders, as they may contain spyware or other malware.
Regularly check account activity and connected apps
Every so often, take a few minutes to review which devices and apps have access to your Google account. Remove anything you don’t recognize or no longer use.
Also, review the list of third-party apps connected to your account. If you see anything unfamiliar or suspicious, revoke its access. This helps you spot suspicious logins early and keeps your account connected only to services you trust.
FAQ: Common questions about hacked Google accounts
Can I recover a Google account without a phone number?
Yes, it’s possible. Even if you no longer have access to your phone, you can still recover your account using other options, like a recovery email or by verifying your identity. Start by selecting “Try another way” during account recovery. This may let you confirm your identity using previously set options such as a backup email, past passwords, or account creation details.
How long do I have to recover my hacked Google account?
There’s no strict time limit, but the sooner you act, the better your chances. The longer someone else controls your account, the more likely they are to change your recovery settings. If you’ve lost access, you can use the “Can’t access recovery email or phone number” method and move through the recovery steps while you still have a chance to prove ownership.
How long does Google account recovery usually take?
It can take anywhere from a few minutes to several days. The time depends on how much information you can provide to confirm that the account belongs to you. If Google can’t verify your identity immediately, you may need to wait while they review your case.
Can a cybercriminal change my Gmail password?
Yes, and that’s often the first thing they do. Once they’re in, they may also change your recovery options to make it harder for you to get the account back. If you think your password has been changed, start recovery immediately by providing your last known password and account creation details to prove ownership.
Does Google notify me if my account is hacked?
Often, yes. Google usually sends an alert if there's suspicious activity, like a login from a new device or location. If you missed the alert or didn’t receive one, you should check account activity and connected apps to review recent logins and app access.
Can I find out who accessed or hacked my Google account?
You won’t see a name, but you can view IP addresses, device types, and locations that recently accessed your account. To check for suspicious access, check account activity, which shows exactly where and when your account has been used.
Is it possible to contact Google support directly?
Yes, but it depends on the service you're using and whether you're a paying customer. For most free Google services like Gmail or Drive, support is limited to self-service help centers and account recovery tools.
If you're a paying customer through services like Google Workspace, you can access direct support options. These are available through your account dashboard and often include faster response times and personalized assistance.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN
















Comments
I cant look up new info on Google anymore on this phone. A horrid snowman icon comes up over what I've searched for after a few seconds and then I'm asked to tell Google what the problem is. This must be a hack as you have never replied. I am using my more hotspot via my Vodafone contract. They don't know what to do.