Are QR codes safe? Learn how to spot and avoid scams



QR codes are an integral aspect of modern-day society, allowing access to digital information like payment portals or restaurant menus with a quick and easy scan.
However, this widespread adoption has made them a prime target for cybercriminals aiming to spread malware, steal data, or commit fraud.
The danger of QR codes lies in their simplicity: a malicious code can appear identical to a legitimate one. Even advanced security tools can't prevent the human error of accidentally scanning a fraudulent code, which means vigilance is crucial.
This guide will equip you with the knowledge to safely navigate QR codes. It explores how they work, uncovers scam tactics, and includes actionable tips to help you identify and avoid malicious codes.
What is a QR code?
A QR code, or Quick Response code, is a two-dimensional code that digital devices can quickly read. Each QR code has a distinct black and white pattern of dots, and each of these dots forms one of up to 177 x 177 encoded modules. QR codes were invented by Denso Wave’s Masahiro Hara and Takayuki Nagaya in 1994, with the aim of making digital code scanning more efficient.
Today, QR codes are versatile tools for instant information sharing, capable of storing a significantly larger amount of data than traditional one-dimensional barcodes. They’re used in supermarkets, restaurants, airports, and many other places.
How does a QR code work?
When you scan a QR code, your device’s camera or a dedicated QR code app captures the image of the code. The software identifies the unique black and white patterns, which encode specific pieces of data. These patterns are then translated into a usable format.
Once decoded, the information triggers an action. For instance, if the code contains a website URL, your phone's browser will open that page. If it's contact information, it might prompt you to save a new contact.
What are the parts of a QR code?
A QR code is generally made up of the following key components: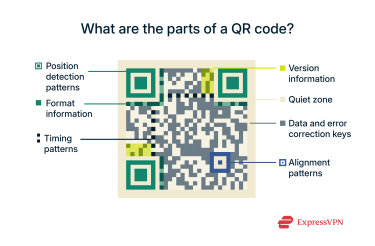
- Position detection patterns: Three large, square patterns located at the top-left, top-right, and bottom-left corners. They tell the scanner the orientation of the QR code, ensuring it can be read from any angle.
- Alignment patterns: Seen in larger QR codes, these smaller patterns help maintain alignment for complex codes, preventing distortion during scanning.
- Timing patterns: These are alternating black and white modules running between the position detection patterns. They provide a coordinate system, letting the scanner determine the size of the data matrix.
- Format information: This area near the position patterns contains data about the error correction level and the data mask pattern used, helping the scanner correctly read the code even if it's partially damaged.
- Version information: This indicates the QR code version, which dictates the overall structure and data capacity.
- Data and error correction keys: This is the bulk of the QR code area, consisting of the actual data you want to convey, interleaved with error correction codes. The error correction keys ensure that the QR code can be scanned successfully even if up to 30% of its surface is obscured or damaged.
- Quiet zone: This is a blank, unpatterned border around the QR code to help the scanner isolate the code from its surroundings and prevent interference from other visual elements.
Types and styles of QR codes
There are different types of QR codes, each with unique characteristics affecting their flexibility, data capacity, and security. Knowing the differences can help you understand how they’re used and where potential risks might lie.
Static vs. dynamic QR codes
One of the main differences between QR codes is whether they’re static or dynamic, but both work the same way. The real difference is what the link inside the code points to.
Static QR codes point directly to a fixed URL or piece of data, like a coupon, a contact number, or a Wi-Fi password. Once created, the link can’t be changed.
Dynamic QR codes are more like a service. A company provides you with a unique redirect URL and generates a QR code that points to it. You can then use that service to control where the redirect URL leads. The service may also offer additional features, like automatically logging requests received at the redirect URL.
So while the QR codes themselves are identical in function, dynamic codes offer flexibility and control through the use of an intermediate redirect service.
Common QR code variants (Model 1, Micro QR, rMQR, Frame QR)
Beyond the static/dynamic distinction, there are several standardized QR code variants, including the following:
- Model 1 and Model 2 QR Codes: Model 1 was the first model of the QR code, capable of storing up to 1,167 numerals with its maximum of 14 modules. Model 2 improved upon Model 1 and is the more commonly encountered standard QR code these days, allowing for up to 7,089 numerals with its maximum of 40 modules. Model 2 is what you typically find on posters, flyers, and product packaging.
- Micro QR Codes: These are much smaller variants, with a maximum capacity of only 35 numerals. They contain only one position detection pattern and are generally used to label small items, like electronic components, product tags, and business cards.
- Rectangular Micro QR (rMQR) Codes: These are rectangular QR codes, designed for narrow spaces where a traditional square QR code might not fit. They have one and a half position detection patterns and are capable of storing 361 numerals.
- Frame QR Codes: These codes have a customizable "frame" area in the center of the code. This central space can display an image, logo, or text while the surrounding QR code still functions for scanning.
Secure QR codes (SQRC): What makes them safer?
SQRCs look like regular QR codes at a glance, but they’re unique because their design lets a single QR code carry both public and private data. Anyone who scans the QR code can access the public information. However, the private data can only be seen by a person who has a specified device that can read it.
This dual-layer structure makes them ideal for things like accessing secure login credentials, distributing sensitive documents, or verifying identities, because unauthorized users can’t access the protected data even if they scan the code.
SQRCs use encryption and controlled access. By incorporating secure elements like public key infrastructure or device-specific access controls, they greatly reduce the risk of spoofing, data leakage, or man-in-the-middle attacks. They’re popular in enterprise and industrial settings, for example, being used for tamper-proof product tracking.
Basically, attackers can’t do anything without the right credentials because the visible QR code doesn’t reveal the encrypted portion. This makes SQRCs a more secure alternative to conventional QR codes in security-sensitive situations.
Why are QR codes used in scams?
 The convenience and widespread adoption of QR codes make them an attractive target for cybercriminals. QR code scams are also referred to as “quishing” (QR code phishing).
The convenience and widespread adoption of QR codes make them an attractive target for cybercriminals. QR code scams are also referred to as “quishing” (QR code phishing).
Rise in QR code popularity and global adoption
QR codes have become ubiquitous, seeing exponential levels of growth in recent years. What began as a niche tool in manufacturing has become a key component of marketing, retail, and logistics worldwide. This widespread integration means that more people are accustomed to scanning codes without much scrutiny.
How cybercriminals exploit QR code trust
The fundamental issue in QR code security lies primarily in users’ tendency to trust what they scan without any verification attempts. Malicious actors exploit this by embedding malicious links in QR codes that lead to phishing websites. Also, they can hijack QR codes by placing fake codes over legitimate ones in public spaces like restaurants or parking meters.
This combination of hidden malicious destinations and potential for physical manipulation makes QR codes a potent vector for exploitation.
Are QR codes trackable?
Yes, but only if they’re dynamic QR codes. In this scenario, any device that scans the code first accesses the redirect server, which then points to the final destination. This interaction with the redirect server can potentially track the number of scans, time and date of scans, and even the location of the scan (based on IP address).
If you’re worried about your location being tracked through QR codes, you can use ExpressVPN to hide your IP address and ensure the redirect server can’t see your real location.
Do QR codes collect personal data?
QR codes themselves do not collect personal data. However, the content that the QR code links to could potentially collect personal data. If a QR code directs you to a malicious website, that website can then attempt to collect your login credentials, location data, device information, and other sensitive details.
Can QR codes be hacked?
A QR code itself is a static image with encoded data, so it can’t be “hacked” like a traditional system. No one can break into the QR code’s structure to alter the information after it’s been generated. However, malicious actors could potentially hijack QR codes by printing malicious codes as stickers and placing them on top of legitimate codes.
Most common QR code scams

1. Codes sent in phishing emails
This scam involves embedding a malicious QR code directly into an email. These emails appear to be from legitimate sources like banks, popular online services, or shipping companies, urging you to scan the code for seemingly legitimate tasks like account verification or package tracking.
Since traditional email filters can’t analyze images as well as text, the malicious QR code often bypasses security checks, making this a common attack vector. Our in-depth guide on phishing emails highlights all the red flags you need to know about to determine if an email is dangerous.
2. Fake QR codes on restaurant tables and menus
Since many restaurants now use QR codes on their menus and restaurant tables, scammers can exploit this by placing fake QR code stickers over legitimate ones. These fake QR codes lead to malicious websites that could potentially steal your personal information.
3. QR codes in public Wi-Fi or free access zones
Public Wi-Fi networks in cafes, airports, or shopping centers are often accessed via QR codes for convenience. Cybercriminals capitalize on this by placing fake QR codes that promise free Wi-Fi access but could lead to the following cyber threats:
- Rogue Wi-Fi connection: The QR code could connect your device to an unsecured or malicious network, allowing attackers to intercept your traffic.
- Malware download: You’ll be prompted to download harmful software disguised as a Wi-Fi configuration file.
- Phishing pages: Malicious QR codes could lead to fake login portals that could steal personal information.
Remember, you should use a VPN on public Wi-Fi to encrypt your data and hide your IP address. ExpressVPN also offers protection against malicious websites via its Threat Manager tools.
4. Counterfeit packaging and tampered labels
Product packaging and labels are also vectors that malicious actors can use for QR code scams. Scammers can copy the QR code of a genuine product and place it onto a counterfeit. When someone scans the QR code on the counterfeit product to verify its authenticity, they’ll be redirected to the official website.
5. QR codes used in banking and payment fraud
The widespread use of QR codes for quick contactless payments makes them a target for financial fraud through the following methods:
- Fake code overlays: These are fraudulent QR code stickers on public payment points like parking meters and fuel pumps that could redirect users to fake payment portals designed to capture credit card numbers or bank account details.
- Fake bill payments: Cybercriminals may send fake utility bills or invoices with a malicious QR code for payment that diverts funds to the scammer's account.
6. QR codes in healthcare and medical fraud
The healthcare sector uses QR codes for patient information, appointment scheduling, and accessing digital health records, but scammers can leverage this to initiate QR code scams. You may receive fraudulent emails or physical letters with QR codes leading to phishing sites designed to steal your sensitive information.
7. Cryptocurrency QR code scams
If you use crypto, you should keep watch for the following scams:
- Fake wallet addresses: QR codes that appear to be for legitimate crypto transactions or giveaways may actually contain the scammer's wallet address.
- Phishing for wallet credentials: QR codes could redirect you to fake cryptocurrency exchange login pages or "wallet connection" services that could steal the private keys to your crypto wallet.
- "Free crypto" lures: You might see links or posts online with QR codes leading to phishing websites that claim to give free crypto.
8. Social media QR code scams
Social media platforms are rife with QR code scams. These include scam QR codes in posts or author bios promising large prizes, free gift cards, or exclusive content. However, scanning these codes leads to malicious websites that may steal your sensitive information.
9. Fake codes in junk mail
Even physical mail isn't safe from QR code scams, as you might receive mail containing QR codes leading to scams. One noteworthy incident is when people received mail claiming to be from MeteoSwiss, the Federal Office of Meteorology and Climatology in Switzerland. The letter asked readers to download a weather alert app, which turned out to be malicious.
10. Fake QR code scanning apps
While QR code scanners are built into most smartphones now, some users might still try downloading third-party apps to scan codes. These can be malicious apps that install malware onto your device or harvest your sensitive data. Always check that the app is from a legitimate developer and has plenty of users and good reviews.
How to stay safe when scanning QR codes
By adopting a few simple habits, you can significantly enhance your safety and scan confidently. The key is to approach every QR code with a healthy dose of skepticism and vigilance. The tips below will help ensure you don’t accidentally scan malicious QR codes.
QR code scanning checklist
Run through this quick mental checklist before you scan any QR code:
- Verify the source: Ensure the QR code you’re about to scan comes from a trusted source.
- Consider the context: Think about whether the QR code makes sense in your current setting. Seeing a QR code on a restaurant table is to be expected, but a QR code stuck on a public wall with no context might be dangerous.
- Inspect for tampering: Physically inspect the QR code to see whether it’s a sticker placed over another QR code. Any alteration signs are a significant red flag.
- Preview the URL: Most built-in smartphone QR code scanners show a preview of the URL when you scan a QR code. Verify whether it’s a legitimate URL before opening it.
Recommended apps for safe QR scanning
The best app for scanning QR codes is your smartphone’s built-in camera app. Most smartphones have scanners in their cameras; just open the camera app and point it at a QR code. By using the built-in app, you can be certain you’re not using a third-party app that monitors your data or potentially has malware.
How to spot a malicious or altered code
There are various telltale flags that a QR code is altered and potentially malicious, including the following:
- Physical overlay: A common indication of a tampered code is that it’s a sticker placed directly over a legitimate one. Check for peeling edges, different textures, or misalignments.
- Poor quality printing: Malicious codes might have low quality, making them appear pixelated, faded, or distorted compared to professionally produced ones.
- Suspicious placement: A QR code placed somewhere odd, like a random lamp post, should immediately raise your suspicions.
- Branding mismatch: If a QR code claims to be from a known company, but the logo or colors seem off, it could be a fake.
- Unrecognized URL: Be cautious if you see an unrecognized URL in the preview upon scanning a QR code.
What do I do if I scanned a suspicious QR code?
Accidentally scanning a malicious QR code can be alarming, but acting quickly can mitigate potential damage. The immediate steps depend on what happened after the scan: did it just open a strange webpage, or did you enter personal or financial information? Below are the essential actions to take if you suspect a scam.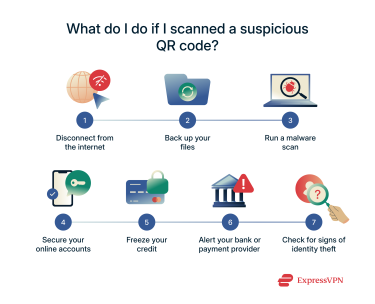
Disconnect from the internet
Disconnecting from the internet serves as your initial line of defense. As soon as you suspect a problem, turn off your device's Wi-Fi and mobile data. This severs any active connection between your device and the internet, preventing potential data exfiltration or the silent download of additional malware.
Back up your files
Prioritize creating a backup of your important files, as having a recent backup ensures all valuable documents, photos, and other data remain safe. It’s ideal to have a preemptive backup available in case you scan a QR code that introduces malware and requires a factory reset. Use an external hard drive or a trusted cloud storage service for this crucial step.
Run a malware scan
Use a reputable antivirus tool to perform a comprehensive full system scan if your device exhibits signs of malware. Ensure that the software's threat definitions are fully updated for the most effective detection and follow its recommendations to quarantine or remove any detected threats.
Secure your online accounts
It’s essential to update your online account information if you suspect a QR code scam, especially if the URL you opened required you to enter any login or account information. Secure your digital presence with the following methods:
- Change your passwords: Immediately update the passwords for your most critical online accounts, like email addresses, banking services, social media platforms, and any payment-linked accounts. Using the ExpressVPN Keys password manager can help streamline this step.
- Enable two-factor authentication (2FA): Enable 2FA on every supported account. This adds a vital layer of security, requiring a second verification method so that even if your primary password is stolen, a cybercriminal won’t be able to break into your account.
Freeze your credit
You should initiate a credit freeze if any personally identifiable information, like your Social Security number or driver's license number, has been compromised. A credit freeze prevents anyone from opening new credit accounts in your name, significantly limiting the damage an identity thief can inflict.
Alert your bank or payment provider
If you’ve entered banking details, credit card numbers, or other banking information, immediately contact your bank and credit card companies and explain the situation. Your bank or payment provider will advise you on the necessary protective measures, which may include canceling compromised cards and issuing new ones.
Check for signs of identity theft
Following a potential data compromise, keep watch for any unusual activity that could signal identity theft. Key indicators include the following:
- Unfamiliar charges on your bank or credit card statements
- Bills for services you don’t recognize
- Unusual calls, emails, or messages regarding accounts you didn't open
Staying vigilant for these signs is crucial. If you’re in the U.S., you can use ExpressVPN’s Identity Defender to defend against identity theft. It provides ID alerts, ID theft insurance, data removal, and a credit scanner, all of which work simultaneously to provide comprehensive protection.
FAQ: Common questions about QR code safety
What is the real risk of QR codes?
The real risk of QR codes is in their ability to conceal harmful destinations behind a simple, scannable image. They can redirect you to phishing websites designed to steal your credentials, download malware onto your device, or facilitate various forms of financial and identity fraud.
How do I know if a QR code is safe?
You can’t tell if a QR code is safe just by looking at it. But there are ways to stay safe, like checking where the code came from, looking for signs of tampering, previewing the link before opening it, and avoiding codes from unknown or untrusted sources.
Can a QR code get hacked?
A QR code itself cannot be "hacked" in the sense of its internal data being altered after creation. However, if it’s a dynamic QR code, its redirect URL can be compromised.
Where should you not use QR codes?
Avoid using QR codes where the source isn’t verified or could easily be tampered with. This includes QR codes in unsolicited emails or physical QR codes in unsupervised public locations.
Do I need an app to scan QR codes safely?
No. Most modern smartphones (both iOS and Android) have QR code scanners built into their camera apps. These native scanners are the safest option, as they’re part of your device's core operating system.
What’s the safest QR code scanner?
The safest QR code scanner is generally your smartphone’s native camera app. If your phone is older and doesn’t have a built-in scanner, choose a reputable and well-reviewed app from your device’s official app store.
Are QR codes safe for payments?
QR codes can be safe for payments when used with trusted payment platforms and verified vendors. However, there’s a risk of scammers replacing legitimate payment QR codes with their own, redirecting your payment to a fraudulent account. Always verify the recipient before finalizing any QR code payment.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN